DEF CON 2025
Ferdinand Mudjialim, Pentester

Attending DEF CON this year with the CISO Global team was a blast as always, despite the searingly hot Las Vegas weather. Luckily, with the recent exodus to the Las Vegas Convention Center, it’s easy to forget that there’s an outside world in the first place. DEF CON is one of the premier cybersecurity conferences and a veritable candy shop for pen testers and other cybersecurity researchers. This year I was able to meet some well-known creators and icons in the hacking space, as well as people from all over the world. There are more people coming from sponsors based out of Singapore, Hong Kong, Korea, and Japan indicating a growing international understanding of the importance of cybersecurity. There were major expansions to the Aerospace and Car Hacking Villages, and the addition of a new Maritime Village. This increased interest in the hacker realm certainly reflects the reality of everything around us, from appliances to transportation becoming computerized and connected. It was a great opportunity to be able to learn from the villages and hackers all over the world, and in this article, I’d like to share some highlights from the many workshops and labs I participated in.

Hacking UAVs and Flight Runways
First stop: the Aerospace Village. In the Aerospace village, hackers and engineers have a playground of systems and software that power airlines, airports, and even space equipment. At DEF CON, there are often many labs that have been designed to have their security purposely vulnerable to attack, with attendees testing their skills to see if they can “hack” or solve the challenge. Two labs in particular caught my eye: the unmanned aerial vehicle (UAV) and flight runway workshops. In the UAV lab, I was tasked with taking apart the UAV, reverse engineering the firmware, putting it all back together again, and hijacking the connection between the controller and mobile app. I had to combine my knowledge of firmware analysis, network communication interception, and even application pen testing to solve the lab. The lab showcased how reliance on Wi-Fi and hardcoded values in the firmware could easily be exploited with the right steps. As drones and other UAVs become more ubiquitous, knowing how to verify they are as secure as possible becomes critically important for safety and privacy.
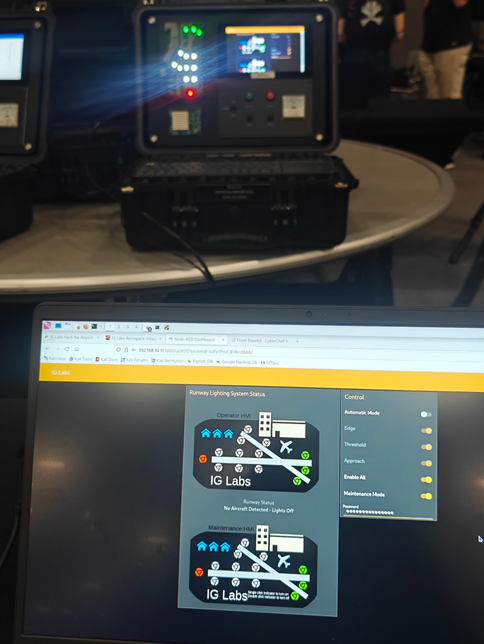
For the flight runway lab, I was tasked with taking control of the runway light system after a simulated attacker had hijacked the Node-RED configuration. If you haven’t heard of Node-RED, it is a web-based flow editor commonly used for connecting hardware devices with web/API services. It becomes a “communication bridge” in which separate, sometimes unrelated system components can be orchestrated to achieve a larger task. I learned how to edit flows in Node-RED, find where attackers can hide malicious logic, and patch the connections between the OPC server (the “bridge” for industrial devices), HMI (Human Machine Interface, i.e. the user interface for controlling the lights), and the physical lights. It’s not hard to imagine how catastrophic abuse of these types of system by cybercriminals or adversarial intelligence services could be if they aren’t properly secured. Well, after applying my “fixes” and making sure I had control of each individual light via the HMI, I became the second person at DEF CON to complete the lab in its entirety. Hopefully, solving these labs demonstrates just how important it is to have critical systems that are capable of being scrutinized by independent cybersecurity professionals.
Cloning and Pwning

While wandering around the smaller villages, I came across a station in the Loong community booth set up with Proxmark and Flipper devices. I’m well aware of these devices as a pen tester and know that they’re used for cloning things like building access cards, RFID tags, and key fobs. Unlike some of my other team mates at CISO Global that specialize in them, I have never used these tools since I don’t own them myself. During the lab, I was able to use small RFID detector tags to determine if the RFID devices were operating on high or low frequencies (HF vs LF). A small LED lit up on the tag when it detected the corresponding field from the reader. After determining the kind of frequency I needed to work with, I fired up Proxmark to read the cards and extract data from them.
Proxmark with example key cards and fobs

I learned that cards usually have some sort of ID plus sectors and blocks of data. One of the cards was a Mifare Classic 1k (HF), and I was able to copy just the UID over to a blank card using the Proxmark. To my surprise, the reader did not verify any other data fields on the cloned card, and the lock opened with minimal effort. I used a similar method of “spoofing” or impersonating the ID to clone an LF tag to open a door lock. It was also quite worrying to learn that most building access systems are in fact that easy to fool as well. Just a few moments in range of a valid key card and an attacker can make a working clone, indistinguishable by the security system (and its access logs) from a legitimate one.
You (CAN) Hack a Car!
To wrap it all up, my final stop was the Car Hacking village. I saw two groups of hackers working on hacking an electric van and truck, but those two particular stations were always in high demand. Given that I knew only basic things about car security, I decided to get a primer from a simulated lab. In the lab, my task was analyzing CAN bus frames with the goal of taking control of the simulated car. A car’s Controller Area Network (CAN) bus acts as the vehicle’s central nervous system, allowing its various electronic control units (ECUs) to communicate with each other over a single shared network instead of complex, heavy wiring. For instance, when you press the brake pedal, a sensor sends a signal over the CAN bus to the brake light controller, illuminating the lights. The breadth of the access it provides makes for a compelling target for hackers.
To start the lab, I initiated my attacks from a provided laptop and used various CAN commands from the can-utils tool to sniff CAN frames as I was controlling the car manually (opening/closing doors, changing the accelerometer, etc.). After gathering the specific CAN IDs and data needed to perform each function, I was able to send the exact frames that would change the state of the car from the attacker laptop. It was surprisingly easy to exploit the inherent security flaws in the CAN protocol. While it is good to prioritize speed and reliability, it comes at a cost. There is no encryption or authentication in CAN data, and even though it is tied closely to the hardware/physical level, it’s not hard to see how an attacker could inject data and perform unwanted or even dangerous actions.
Conclusion
Attending DEF CON every year is a reminder to me that security will always be a two-way street. Defenses are always improving over time, but cybercriminals work hard to be one step ahead. No matter what the platform or system is, determined threat actors are going to find a misconfiguration here or a vulnerability there. It’s up to manufacturers, engineers, and security professionals to learn from the oversights and lead the way to a more secure future.