
CISO Edge Cloud Security Platform
Managed Secure Service Edge

Secure Your Most Valuable Cloud Assets
Many organizations today contend with a patchwork of security solutions designed to protect traditional on-premises networks. With the rising popularity of remote workforce, BYOD, and cloud first applications, organizations struggle to extend their security fabric to these emerging environments. As more business critical workloads migrate to the cloud, this mismatch of security solutions leave critical gaps in security visibility that are often targeted by today’s threat actors.
Remote access and cloud computing offer tremendous upsides for organizations and employees, but they also make great targets for attack.
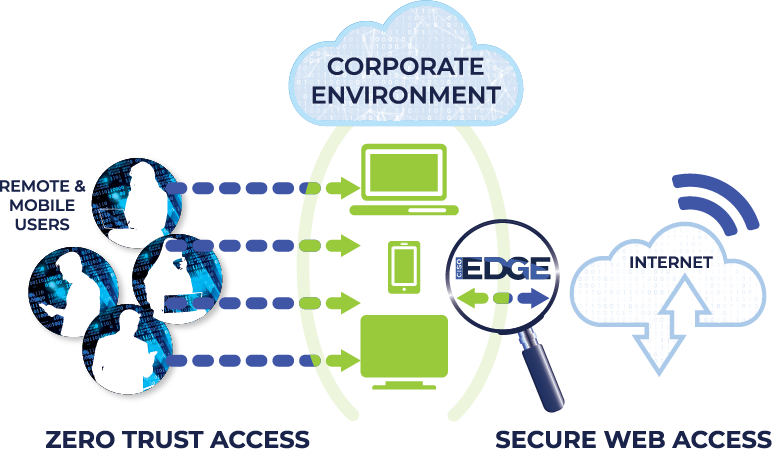
Secure Your Remote Work Force
Users working from home or on the move operate outside the boundaries of traditional on-premises security controls. It’s vital to ensure your users are secure no matter where they are and so your security controls must evolve to provide coverage beyond your enterprise network. CISO Edge is designed as a cloud centric security solution that can apply your organization security policies to your users no matter what network they are on.
The most used software by users is their internet browser, however the browser is also the most targeted piece of software by attackers. While on the Internet, your users are constantly bombarded by privacy invading trackers, web-based malware, and drive by attacks. The same web browser they use to login to critical business applications may also have a tab open to a popular social media website or another untrusted Internet site. CISO Edge provides a layer of security and control for your user’s Internet browsing by isolating the browser from their workstation and your critical business application ensuing browser-based attacks cannot be used to compromise your environment.
Speak With a CISO Global Security Specialist Today
Our experts maintain the most respected credentials in the industry across cybersecurity, risk and compliance, forensics, incident response, ethical hacking, security engineering, and more.