The Argument for Enterprise-Wide Ad Blocking
Chris Clements, VP of Solutions Architecture at CISO Global
The concept of enterprise-wide ad blocking always provokes a powerful response. Whenever I suggest, even casually, that the next step organizations should take to improve cybersecurity posture is implementing enterprise-wide ad blocking, I can hear the collective screams of sysadmins and help desk personnel everywhere — Websites could have compatibility issues! How will we manage it? Users won’t understand! It could be a help desk nightmare!
And you know what? They are absolutely right.

Ad blocking at the enterprise level has its challenges, as do all security advancements. Multifactor Authentication (MFA) had similar challenges, and yet, organizations that have moved beyond user-chosen passwords as the sole security measure for cyber attacks and adopted MFA significantly improved their cyber resiliency. Ad blocking, in a similar fashion, provides a broad extra layer of defense for online activities.
Ad blockers work by denying access to undesirable content on the web and despite the name, they do more than just block ads. Ad blockers have the ability to filter out threats including malware, privacy invading surveillance networks, and other malicious activities.
Seemingly harmless and ordinary, the most dangerous daily activities that most of us do online are reading email and browsing the web. However, both activities give threat actors contact points with our computers that would otherwise be difficult or impossible for them to reliably gain. Attackers focus on leveraging these contact points to conduct cyber attacks.
Ad blocking is a powerful tool to we can implement to filter out content that can invade privacy and security settings. In the following sections, I will give examples for each, but first, I would like to share the success that implementing enterprise-wide ad blockers can bring:
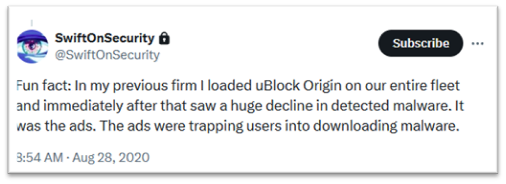
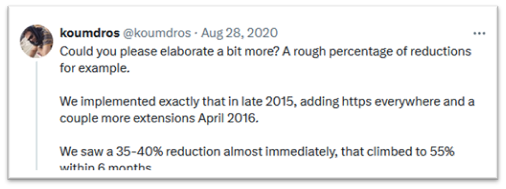

It’s worth noting that the potential impact of enterprise-wide ad blocking on cybersecurity is significant, particularly relative to its implementation complexity. Let’s explore some areas where users can be protected by ad blockers.
1. Outright Malvertising
The first category of threats is malicious use of advertising networks or “Malvertising.” These are outright campaigns by threat actors who insert malware and phishing links into ad networks. This type of attack occurs when cyber criminals leverage the advertising networks that distribute ads to many internet sites, including search engines, social networks, and even blogs and merchants. By fooling the ad network into inserting their malicious links in place of legitimate advertisements, the threat actor can lure unsuspecting users to click links that install malware or attempt to phish sensitive information such as passwords, from victims:
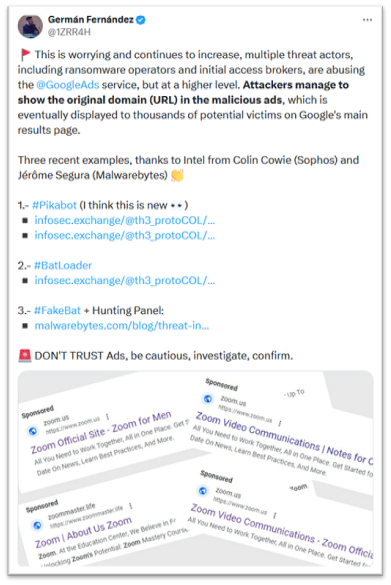
Malvertising campaign masquerading as Zoom
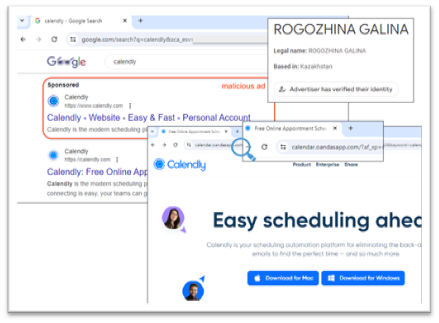
Malvertising impersonating the Calendly app
2. Adware / Scareware Buttons and Links
Savvy internet users who’ve browsed the web long enough, have seen a scourge of fake buttons. These are usually presented as download links on otherwise legitimate software distribution websites. More common are “coupon” hunting packages, or software advertised as “necessary” to open or create certain files, some of which monitor and resell a user’s browsing behavior. Unlike overt malvertising, these types of fake buttons and adware links don’t rely on fooling the ad network distributing the ads. Instead, they pay the website to present them alongside the real content. In this way, sites hosting these buttons and links are actively complicit in deceiving their users into falling for the scam.
Because knowingly helping a cyber criminal distribute malware would likely carry the risk of legal prosecution, these usually lead to software packages that aren’t outright malware. However, they deliver various unwanted behaviors such as recording and sending user activity to untrusted third parties, nagging the user to buy fake antivirus software, or inserting yet more ads into the victim’s browser or operating system. While irritating on personal or home computers, at work they become more problematic as they can expose sensitive organizational data. By preventing users from encountering these types of deceptive software packages, ad blockers significantly reduce the risk of exposure and potential infection.

Depiction of common fake software download links
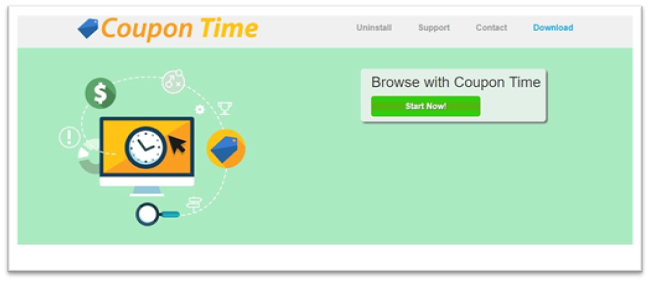
Coupon app example
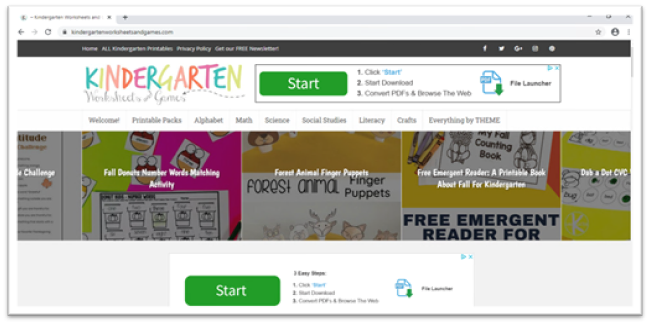
Ad infested software download seemingly “required” to open the files shown
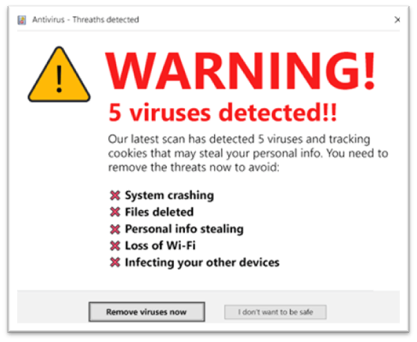
Scareware for fake antivirus software
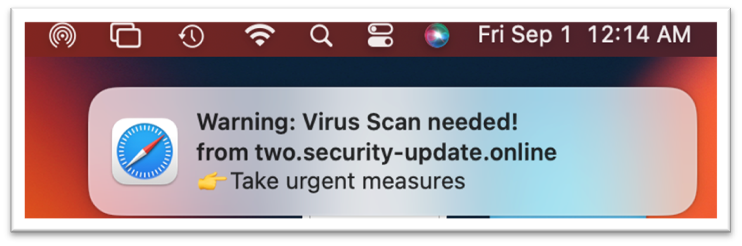
Fake system notification from a site that has tricked a user into “allowing notifications” from a scammy site
3. Privacy Invasive Ad Networks
The prior examples focus on the malicious use of advertising to harm users, but they also harm cybersecurity defenders looking to protect their organization from active cyber attacks. Ad networks utilize a myriad of techniques to track and target users:
- Session-Based Tracking — Monitoring user sessions during a single visit to a website. They track the pages visited, interactions, and time spent. This data helps create user profiles for targeted advertising.
- Client Storage Tracking — Utilizing browser storage mechanisms such as cookies, localStorage, or sessionStorage, these store information locally on the user’s device, allowing ad networks to recognize returning visitors.
- Client Cache Tracking — Ad networks leverage browser caches to store temporary data. By examining cached resources, they can infer user behavior and preferences.
- Fingerprinting — Fingerprinting involves collecting unique attributes from a user’s browser, such as browser type, screen resolution, installed fonts, and plugins. These attributes create a distinctive “fingerprint” that helps identify users across different websites.
- Others — Some ad networks use additional techniques, including pixel tracking, referrer headers, and user agent strings. These provide further insights into user behavior and preferences.
Many of these techniques come suspiciously close to how real malware operates:
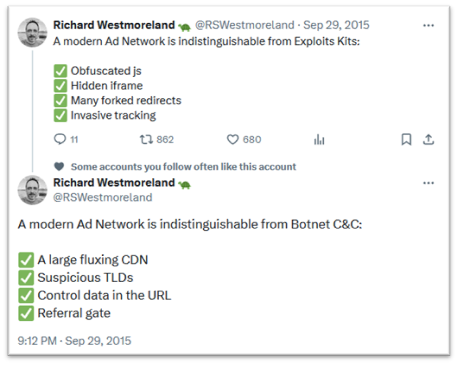
Examples of how ad networks can add unnecessary noise to a security analysis.
This type of noise makes the defenders’ job much harder. At best it adds unnecessary time to investigating whether or not an event is a real threat, and at worst it could lead to the false negative detection of a real malware event improperly identified as ad network traffic.
User Experience and Performance and Best Practices
These examples show some of the cybersecurity specific threats that malicious ads present to organizations. Ad blocking technology adds an extra layer of protection to mitigate those risks. Although they are primarily used for their quality-of-life improvements when browsing websites — by blocking auto-playing ads, distracting pop-up windows, and general tacky clutter that can make modern web surfing actively hostile — they also generally improve both network and system performance. After all, an ad that is blocked is one that doesn’t have to be a) downloaded from the internet or b) rendered by the user’s browser. Here’s an example from the ad blocker on my home computer:
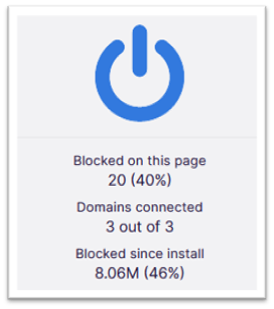
Statistics reporting ad blocking’s effect on my browsing. Yes, that’s nearly 40% of the current
page being saved from being processed as well as 46% (!!) of my total browsing usage since install.
The added efficiency is a nice benefit, but did you know that ad blocking is now considered by CISA as a cybersecurity best practice? Hopefully I’ve made a compelling case for the benefits of ad blocking technology in an enterprise environment. If this makes sense for your organization, the next steps are determining your approach to implementation.
Choosing an Ad Blocker
Ad blockers generally come in two varieties, browser level and network level. Each has unique capabilities and considerations that need to be considered to determine if one or both are right for your environment.
Device-Level Ad blockers
Device-level ad blockers work by installing and configuring additional software on user devices. Most often, this takes the form of an add-on or extension to a web browser that can monitor and modify all web content. For mobile devices this can sometimes take the form of an app that configures a “fake” VPN connection that redirects any destinations in its blocklist to a non-existent blackhole.
Of these two, the browser add-on method is by far the most powerful and configurable. By integrating with the web browser directly, browser-based ad blockers can implement fine grained blocking of web content, including ads that are served as part of a website’s own domain, as well as annoyances such as cookie acceptance prompts. Browser based blockers can also be configured to whitelist content on a one-time basis or allow access for some users but not others such as a marketing department.
These advantages make browser-based blocking attractive, however, at the time of this writing, the deployment and management of browser-based extensions isn’t as straightforward a process as other enterprise software. Though there are recent and notable exceptions to this, deploying browser add-ons, and especially modifying their configuration, has required high level IT expertise to implement in business environments. Hopefully this situation will continue to improve over the coming years, but that largely depends on the adoption rate of ad blocking technologies in enterprise organizations.
Another important consideration when using browser add-ons or extensions for ad blocking is that these are third-party pieces of software with deep and powerful access to sensitive browsing data, usually with no guarantees about future support or changes in developer ownership. If browsers are configured to automatically update these software add-ons without notice, as is a default setting for most, it can put organizations at risk if either the developer or the add-on distributor become compromised. Unfortunately, not all ad blockers are created equal. Some, like the popular uBlock Origin browser add-on, are free and open source, with a developer that has expressed strong opinions on protecting user privacy. Ironically, others are actually in the business of harvesting and selling user-behavior data. Finally, there are commercial solutions available as well, such as AdGuard.
Device Level Ad Blocking Advantages and Disadvantages
Advantages
- Can see and block far more unwanted content than any other solution
- Highly and individually configurable
- Easy fallback if multiple browsers are installed and only the default runs the ad blockers. Users can simply open the secondary browser to validate if the ad blocker is interfering with legitimate content.
Disadvantages
- Limited centralized management capabilities
- Third-party extension ownership can change without notice, with subsequent updates potentially introducing unwanted or even malicious changes to functionality
- Browser variations mean that some browsers support different features for add-ons that can make experiences from browser-to-browser non-uniform
Network-Level Ad Blockers
Network-level ad blockers work either as inline components such as network firewalls, blocklist integrating with DNS servers, or outbound web proxies. In the case of firewalls, some have the functionality to block the initial connection setup to unwanted domains. For DNS ad blocking methods, the DNS server is configured to return either a local loopback address for unwanted domain names, which fails immediately, preventing the associated content from loading, or by displaying a placeholder that indicates ad content has been blocked or replaced.
Of these two methods, DNS has slightly more coverage than inline blocking, but both are limited in effectiveness, as they are only capable of blocking whole domains and not granular website components as most are served over encrypted https. For example, if visiting a fictional news site — “somenewsite.com” loads ads from a third-party domain like “someadnetwork.com” — we can configure our network blockers to break the connection to “someadnetwork.com” to block ads, however, if the ads are part of the base domain of “somenewssite.com” we can’t use a network-based approach to filter those out without blocking the news site itself. This all-or-nothing blocking per domain approach also makes the process of making user exceptions nearly impossible as well. On the other hand, doing so at the network level doesn’t require any additional software or configuration on end-user devices. In contrast, outbound web proxies that completely mediate web communication offer more in-depth ability to perform blocking as they perform a “man-in-the-middle” approach that gives access to cleartext web data, even for encrypted https connections. Outbound web proxies do have their downsides, however. First, they require special organization wide configuration changes to implement, including installing a new trusted certificate on endpoints that allows the proxy to decrypt, inspect, then re-encrypt user web traffic. Second, because this configuration effectively “breaks” end-to-end encryption on purpose to allow for inspection, it exposes all user communications to the proxy server, including potentially sensitive information like healthcare, financial, or other personal information that organizations do not want to have responsibility for.
Exceptions to these network-based approaches are ad blockers for mobile devices that divert unwanted domains to a “fake” VPN connection that simply blackholes the domain-based connection to a known advertising domain in a similar way, however, this does require additional software installation and configuration. The combination of domain-based blocking limits with the additional software and configuration needed typically makes this approach the worst of all worlds, but if it is your device’s only option, it is worth considering.
Deploying these solutions will vary by each organization’s environment, with inline firewall-based solutions being dependent on vendor capabilities and licensing requirements. DNS solutions can take the form of blocklist integrations with Microsoft Active Directory’s built in DNS server, or setting the upstream resolver to a system or service that integrates advertising blocklists. There are also third-party projects like the humorously named “PiHole” designed to run DNS resolution for whole networks with built-in blocklists to prevent access to domains known to serve advertisements. Proxies, for the downsides listed above, are a rarity in today’s IT environments.
Network-Level Ad Blocking Advantages and Disadvantages
Advantages
- Does not require additional software or configuration on individual user endpoints
- Works for all devices on the network, including those that do not support installing ad blocking software locally
Disadvantages
- Limited to whole domain blocking, cannot see individual website components
- Users using custom DNS servers can bypass protections
- Only works for systems on your local network. Once devices leave or connect to cellular networks, they change firewalls or DNS servers and lose protection.
- Failure mode can be transparent if ad domains are redirected to local loopback addresses, making some content appear to be broken, as it simply doesn’t load.
Conclusions
Cybersecurity resiliency requires many layers and controls to be effective. Secure network design, proactive systems and application hardening, detection and response capabilities, as well as frequent validation through exercises like penetration testing are all important parts of a well-rounded cybersecurity program. Would ad blocking be the first order of business for an organization with an immature cybersecurity posture? Definitely not. Once you’ve gotten those big fundamentals addressed though, ad blocking gives you a surprisingly effective additional layer of defense. Ad blocking, while not yet mainstream in most business networks, offers tremendous cybersecurity and end user quality of life improvements, but currently there are only a few commercial solutions available and for both those as well as the free open-source options there is no “click this button and done” implementation story. Despite that, the benefits warrant investigating whether organization wide adoption of ad blocking is possible and how difficult the process may be. Choosing and implementing ad blocking technology, including whether on-device, network-wide, or a combination of both involves weighing the pros and cons. Ad blocking may not currently be the easiest project for an organization to tackle, but the benefits are simply too good not to warrant an earnest try.

About the Author
Chris Clements, CISSP, CCSA, CCSE, CCSE+, CCSI, CCNA, CCNP, MCSE, Network+, A+, began working in the information security field in 2001, and has a wide range of experience with information security technologies including:
- Firewalls
- Intrusion Protection Systems (IPS)
- Intrusion Detection Systems (IDS)
- Virtual Private Networking (VPN)
- Anti-Malware
- Strong Authentication
- Disk Encryption
Chris is also an expert in information security design, security compliance, and penetration testing (ethical hacking) techniques such as:
- Vulnerability Assessment
- Man in the Middle Attacks
- SQL Injection
- Cross Site Scripting
- Phishing
- Secure Environment Breakouts
- Privilege Escalation
- Password Interception
- Password Cracking
He has worked to secure hundreds of customers across North America, from Fortune 500 companies with billions in revenue to small businesses with just a few users. He has developed in-depth security auditing and penetration testing products and service offerings and engaging end-user security awareness programs. Chris also enjoys teaching and has led courses on information security for hundreds of students. With his unique skill set and background in both technical operations and business management, Chris has strengths in business management, sales, and product and service delivery.