Increased Cybersecurity Attacks and New Predators
By: Kerry McQuarrie, Threat Hunting Specialist and Network Operations Center Manager, at Cerberus Sentinel
An alarming number of data breaches are reported each year that are the direct result of sophisticated and coordinated cyberattacks. According to the CrowdStrike 2022 Global Threat Report, cybersecurity risk has been increasing in three distinct areas, (a) endpoints and cloud workloads, (b) identity, and (c) data. Resulting from COVID restrictions, remote work and virtual collaboration has markedly increased; could deepfakes represent a new frontier in sophisticated fraud.
Moreover, as adversaries move beyond malware, malicious attacks can be achieved without writing malware to the endpoint. Instead, legitimate and built-in tools are used to evade detection by legacy antivirus software. This approach, known as LOTL or “living off the land” presents a “malware-free” event that can cause significant disruption to your business operations. During LOTL attacks, threat actors use covert tactics to remain undetected in an environment by leveraging built-in operating systems tools to make them appear as legitimate users in a given organization.

The Changing Landscape of Cyberattacks
Recognizing that your organization has potential vulnerabilities is perhaps more important than trying to determine the motivations of a malicious actor. The biggest ransomware attacks of 2021 were widespread, costly, and industry agnostic.
The Colonial Pipeline Ransomware Attack severely disrupted gas supplies up and down the East Coast of the United States using a compromised password. This attack targeted Colonial Pipeline’s billing system and internal business network, leading to widespread outages, higher gas prices, and lack of available gas. The Russia-linked cybercrime group known as Darkside, extorted a $4.4 million in ransom from Colonial Pipeline shortly after the attack.
According to the Identity Theft Resource Center, in Q1 of 2022 data breaches have increased, but victim rates have declined. Healthcare, Financial Services, Manufacturing & Utilities, and professional service sectors have experienced the most compromises from cyberattacks, with phishing and ransomware attacks at the top two causes for data compromises.
Threat Activity
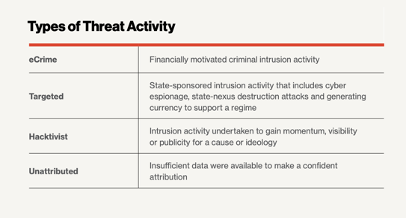
Types of Threat Activity can vary. Significant incidents over recent years include these common threat types: eCrime, Targeted, Hacktivist, and Unattributed or unknown activity.
Active Threats Require Active Threat Hunting
Good cyber-hygiene and the creation and deployment of a cybersecurity culture in your organization will help mitigate the costly effects of a data breach on your operations and possible irrevocable damage to your reputation.
With the increasing popularity and widespread adoption of cloud computing comes the essential need to not only better understand the benefits of cloud computing but also to understand how to best manage your digital infrastructure. Cybersecurity Services including managed detection and response, system monitoring, incident response, penetration testing, and active threat hunting can help to ensure a robust and thriving IT environment.
Creating a Culture of Cybersecurity
Fighting cybercriminals involves three essential components: people, processes, and technology working together to keep your data and your organization safe, with every person involved in the company aware of potential threats as well as behavioral risks. Creating a culture of cybersecurity that can help safeguard your organization has never been a better idea.
To better understand how to safeguard your organization’s data and reputation, reach out to Cerberus Sentinel today.