Demystifying the Dark Web and DarkNets, Part V—FINs, APTs, Rogues, Hacktivists, Cyber Warriors, and Accidentals

Demystifying the Dark Web and DarkNets, Part V
FINs, APTs, Rogues,
Hacktivists,
Cyber Warriors,
and Accidentals
Author: Anonymous Hacker, as told to Lindsey Watts
PREFACE:
In our last installment of this series, we were introduced to some dangerous characters one might encounter on darknets. This week, we will finish out that list, looking into both organized groups and individuals. Wrapping my head around why people do what they do, and how they execute operations that end up costing corporations millions, is always fascinating.
I can’t really say how many times I have glanced at my smart TV with regret since realizing how very vulnerable all of us are to anyone with enough malicious intent and skill to break the perceived barrier of our personal safety. Hacking is very real, and I think due to unfamiliarity with how and why people do it, we “muggles” can become callous to the potential personal effects it can have. The danger here is that we become fatigued from the heaviness of worry, leaving behind our better instincts for self-protection and failing to be as vigilant as we could be.
Five or so years ago, I worked with someone who had recently graduated from a renowned cybersecurity program at the University of Tulsa. Building on his studies, as well as several years of experience as both an intern and a new compliance specialist, he wisely observed that people don’t apply cybersecurity awareness training until they realize how much it affects them, personally. This changed how he approached awareness training for corporate groups. He started teaching people how to lock down their Facebook and Google accounts first, showing them how damaging a compromised account could be for them, their friends, and their families. From here, he applied that base knowledge to their corporate environments and introduced new skills.
I’ve come to realize that my own cybersecurity skillsets need to improve, and much of that journey has been furthered by these interviews. In that vein, I’d like to express my great appreciation to our source for this series. Further, know that I’m starting my own hacking journey in the coming weeks, because as this person has taught me – “If you don’t really know all the ways to break in, you’ll never be able to sufficiently secure your environment.”
One important bit of information uncovered in this interview is how far off our standard news sites can be from the truth. LockBit, Revil, Darkside, and BlackMatter are three other well-known ransomware groups, but during research I observed and pointed out to our source that numerous Clearnet sites report these as attack strains (not groups), and others incorrectly associate Ryuk with FIN 6, rather than FIN 7. We deduced that what must happen is that one reporter cites a source who doesn’t actually know what happens on the DarkNet, but wants notoriety for their firm. Then other reporters begin to cite their work in future articles, building their search engine authority. This false authority drives widespread misinformation that leads career hackers to laugh a little bit at the absolute lack of awareness we non-hackers can have when trying to understand who is attacking us and why. A clever malicious hacker is likely to be emboldened by such misunderstanding, because it shows just how far away blue teams are from a) a steady stream of correct information and b) building a viable defense strategy that will keep them out. This breakdown will only change when organizations can match their attackers’ level of commitment and effort that gets been put into who, how, and what to hack for financial. In other words, when you understand the degree to which these people are willing to go, you understand the degree to which you must protect yourself. This is what we call a “threat informed” strategy at CISO Global.
Without further ado, organized hacking groups and unwitting participants–
FINs: FINs are a subcategory within Cyber Criminals who hack for financial gain and generally target hospitality, retail, entertainment, insurance, technology, chemical, and finance industries. If you read many articles about major hacks, you have likely noticed a trend: Certain Fin hacking groups tend to target certain sectors, but not others. The reason for this is that Fins tend to be associated with organized crime (read mafia). They are well-funded, well-orchestrated, and operate in some of the same ways legal businesses do. There are even some FIN ransomware groups that have tech support lines for people who have paid their ransom, been granted decryption keys, and are struggling to get their environment restored. Some victims report “elevator music” on hold lines while waiting for tech support. Of course, when you are dealing with organized crime groups, there is no guarantee that any promises made will be honored. That all depends how they are feeling about a particular victim on that given day. Nevertheless, similarities to legitimate business operations strike many people as ironic.
Historically, mafia families are known to have historically divided neighborhoods, cities, and even certain types of crime into “territories” with the purpose of preventing family-on-family street wars. So, it only makes sense that the same sort of approach to dividing industries has been negotiated among Fins. One group might negotiate for healthcare, where another might agree to target finance and insurance. And for the most part, as long as everyone stays in their own lane, this practical concession allows everyone to continue to operate.
Fin7, a Russian speaking hacking group also known as Carbanak and Carbon Spider, is one such example. Known to have over 200 employees, this particular group is believed to have authored an endpoint detection and response (EDR) evasion tool for the ransomware group called Black Basta. These groups often purchase services from one another and may even form partnerships, similar to how organizations work together in the legal business world.
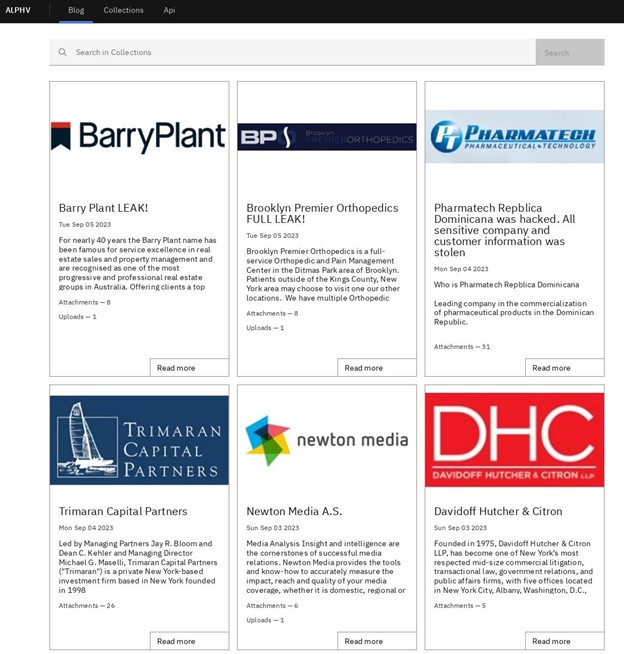
The hacking group ALPHV, also known as Blackcat, posts a collection of its notable data heists on the DarkNet.
FIN6, also known as Skelaton Spider and MageCart, became notorious for successfully stealing credit cards through point of sale (POS) systems in retail and hospitality establishments. This is how Home Depot’s systems exposed customer credit cards in over 2000 stores, ultimately costing them nearly $40 million in lawsuits and settlements in 2015, not to mention the violation of customer trust and their associated personal losses.In 2018, FIN6 appeared to pivot to include ransomware tactics in its arsenal.
APTs
APTs are state-sponsored groups who launch advanced persistent threat (APT) attacks. These are characterized by the attackers’ ability to gain initial foothold, after which they quickly turn to cover their tracks. This allows them to then navigate undetected in systems over a longer period of time than a quick hit attack. APT groups may be looking for valuable data to steal, laying groundwork for future attacks, or executing any number of other malicious activities. Regardless of tactics or tools, one thing is sure – an APT is not something you want, and these groups generally don’t leave without getting what they came for. Due to their targeted nature, APTs tend to be much costlier than other attack types, and those who perform them tend to have a higher level of hacking skills. To go in and move around silently, remain unseen, get what you want, and get out without detection requires another skillset than most hackers have, and it makes them much more dangerous.
The Solar Winds attack is an excellent example of an APT. A third-party software was exploited to gain access to countless corporate, as well as government agency systems. Over a long period of time, espionage was conducted to gather intelligence that could be used for any number of purposes.

Ransomware group LockBit advertises data it has stolen and leaked to DarkNets. Note their Twitter link, contact information, and collection of press about their activities available in the menu.
Rogues
These attackers are extremely powerful and dangerous, because they operate alone or in small groups. This allows them to operate in a very nimble way, leaving an extremely small footprint. If they are skilled enough at what they are doing, they can execute highly complex attacks on their own and may never get caught. Whereas a FIN or APT is an organization with numerous members who can potentially be discovered, tracked, and maybe even turned as informants, rogues don’t have partners. They can disappear more easily, and there are fewer people who could make a mistake or expose them along the way. Independent hackers have DarkNet communities where they share tools, provide or seek mentorship, learn strategies, and access “borrowed” relevant information that has been exfiltrated. These hackers may be small in number, but once they get in, they can do the same amount of damage as any other hacker – even large groups.
Hacktivists
Hacktivists are essentially digital vigilantes. They aren’t looking for financial gain, and they aren’t part of organized crime syndicates or APTs. (Though, that doesn’t preclude some APT or FIN members hackers from also being hacktivists in their free time.) When an issue is important to them, and circumstances for those who they see as being on the right side of that issue become desperate, hacktivists take action. They may be interested in making a point, bringing an issue to the spotlight, or stopping events that they see as unjust. Likely, they will also publicize their actions in hopes of exposing wrong-doers and changing public opinion about truths that were previously hidden.

Members of the group Anonymous appear in public in 2008
wearing Guy Fawkes masks.
Hacktivists like the group Anonymous often fight back against entities or leaders they see as bullies in the modern world. This may include a large country invading a smaller one without provocation, or a corporation that has a terrible human rights record, but it especially includes anyone who seeks to censor. Anonymous and other “hacktivism” groups have taken on nearly every viable large government in existence today, and a long list of corporate targets, proving to be both unstoppable and untraceable on a wide scale. Often portrayed in movies, these groups stand as a warning to powerful people who see themselves as above accountability.
Cyber Warriors
These people hack for more patriotic, moral, or religious reasons. The best bet is to stay off their radar by living in relative peace with your fellow humans. However, cyber warriors may also target nation states they see as in conflict with their personal belief system(s). Additionally, this group is well represented in government cybersecurity and defense groups whose purpose is to help protect their home country’s way of life. Much like a traditional military, they act as a coordinated “army” that takes out targets, defends sensitive assets, etc., under the direction of commanders.
Accidentals
The accidental hacker is someone who either stumbles upon or accidentally creates a hole without any knowledge or ill intent. For example, if an IT administrator makes changes to settings, rolls out new systems, or otherwise stores data in an accessible location, they have essentially created a “hole” to the outside world of hackers, making it possible for them to exfiltrate the data. A prominent example occurred when the IT team at the Oklahoma Securities Commission left 7 terabytes of sensitive data completely exposed due to incorrect configuration settings. According to researchers, “the data was exposed via an unsecured rsync service at an IP address registered to the Oklahoma Office of Management and Enterprise Services, allowing any user from any IP address to download all the files stored on the server.”
Accidentals are still considered hackers, because their actions are initially undetected and went undiscovered by the organization for whom they work. While the breach may have been completely unplanned and unintentional, they bear responsibility for their actions and/or oversights. In this scenario, a stumbler is someone who is simply navigating a web application, perhaps trying to make an online order or take another innocuous action, and they stumble upon a flaw, oversight, poor coding, or other issue that creates a way for them to abuse the intent of the app or code for their own gain. This could include anything from discovering a setting oversight that accidentally sends too many products for each purchase, to information that can be exfiltrated and misused or sold.
If you would like to speak with an expert about testing your incident response plan to make sure you don’t have any gaps that could lead to failure during a real attack, you can reach out to us here anytime. We have the right people on-hand to help.